How should bitcoins approach quantum computing?

In the early 2020s, quantum computing was in the public eye as a potential threat to Bitcoin. Based on the SHA-256 cryptographic hash function, based on the consensus of its operating network, Bitcoin’s value is based on computing power.
If technology exists to bypass the traditional binary system of 0s and 1s for units of information, there is potential to enhance cryptography as we know it. But is this fear exaggerated?
Could quantum computing one day make Bitcoin a meaningless piece of code? Let’s start by understanding why Bitcoin relies on cryptography.
Bitcoin bits and hashing
When we say that the size of an image is 1 MB, we say that it contains 1,000,000 bytes. Since each byte contains 8 bits, this means that the image contains 8,388,608 bits. As a binary digit (bit), it is the smallest unit of information, 0 or 1, that builds the entire edifice of our digital age.
In images, the bits in a 1MB file assign a color to each pixel that can be read by the human eye. In a cryptographic function such as SHA-256 (Secure Hash Algorithm 256-bit) developed by the NSA, it outputs 256 bits (32 Bytes) as a fixed length hash from an input of arbitrary size.
The main purpose of a hash function is to convert any string of letters or numbers into an output of a fixed length. This obfuscation makes it ideal for compact storage and anonymous signatures. And since the hashing process is one-way, hashed data is effectively irreversible.
Therefore, when we say that SHA-256 provides 256-bit security, we mean that there are 2256 possible hashes to return. When Bitcoin payments are made, each Bitcoin block has its own unique transaction hash generated by SHA-256. Each transaction within a block contributes to this unique hash because they Merkle rootsplus a timestamp, nonce value, and other metadata.
A prospective blockchain attacker uses hashes and get the necessary information not only for the block containing the transactions, but for all subsequent blocks chained to it. Needless to say, 2256 possible downloads would create an impractical computational effort, requiring a large expenditure of energy and time, both of which are very expensive.
But could this no longer be the case in quantum computing?
A new quantum paradigm for computing
Moving away from bits as 0s and 1s, quantum computing introduces qubits. Using the observed property of superposition, these units of information can be not only 0 or 1, but both at the same time. In other words, we are moving away from deterministic computing and toward deterministic computing.
Because qubits can be entangled and superimposed, calculations become probabilistic before they are observed. And since there are always more states than 0 or 1, a quantum computer is capable of parallel computing because it can process 2n states simultaneously.
A classical binary computer must run the function for each of the 2n possible states, a quantum computer can evaluate simultaneously. In 1994, mathematician Peter Shore developed an algorithm with this in mind.
Shor’s algorithm Combines Quantum Fourier Transform (QFT) and Quantum Phase Estimation (QPE) methods speed up the pattern search and would theoretically break all cryptographic systems, not just Bitcoin.
However, there is one big problem. If quantum computing is probabilistic, how reliable is it?
Coherence Stabilization in Quantum Computing
When you say the qubits are superimposed, it’s like visualizing the flip of a coin. While in the air, you can imagine that the coin has both positions – heads or tails. But after landing on the ground, the state will decide on a result.
Similarly, when qubits are solvated, their state returns to the classical state. The problem is that an established algorithm like Shor’s requires many qubits to maintain their superposition for a long time to interact with each other. Otherwise, necessary, useful calculations will not actually be completed.
In quantum computing, this refers to quantum decoherence (QD) and quantum error correction (QEC). Furthermore, these problems must be solved over many qubits for complex computations.
according to Millisecond coherence in a superconducting qubit paper Announced in June 2023, the longest coherent qubit time is 1.48 ms with an average gate reliability of 99.991%. The last percentage refers to the overall reliability of the QPU (Quantum Processing Unit).
Currently, the most usable and powerful quantum computer appears to be IBM The quantum system is the second. A modular system ready to scale, Quantum System Two is expected to perform 5,000 operations with three Heron QPUs on a single circuit by the end of 2024. By the end of 2033, this should increase to 100 million operations.
The question is, is this enough to implement Ball’s algorithm and break Bitcoin?
QC risk viability
Due to decoherence problems and fault tolerance, quantum computers have not yet posed a significant threat to cryptography. It is unclear whether a large-scale fault-tolerant quantum system can be achieved when such high levels of environmental cleanliness are required.
This includes electron-phonon scatteringphoton emission and even electron interaction. Moreover, the greater the number of qubits needed for Shor’s algorithm, the greater the decoherence.
However, although these seem to be intractable problems inherent in quantum computing, great progress has been made in QEC methods. in the case Riverlane’s Deltaflow 2 The method performs real-time QEC for up to 250 qubits. By 2026, this approach should lead to the first viable quantum application with a million real-time quantum operations (MegaQuOp).
According to AVS Quantum Science, it would take 13 million qubits to crack SHA-256 in one day. article Published in January 2022. Although this poses a threat to Bitcoin wallets, many more qubits will be needed, around 1 billion. 51% attack Bitcoin has a reputation.
When it comes to implementing Grover’s algorithm, which is designed to use QC to search unstructured databases (unique hashes), scientific work No quantum computer announced in 2018 predicted that it would be possible until 2028.
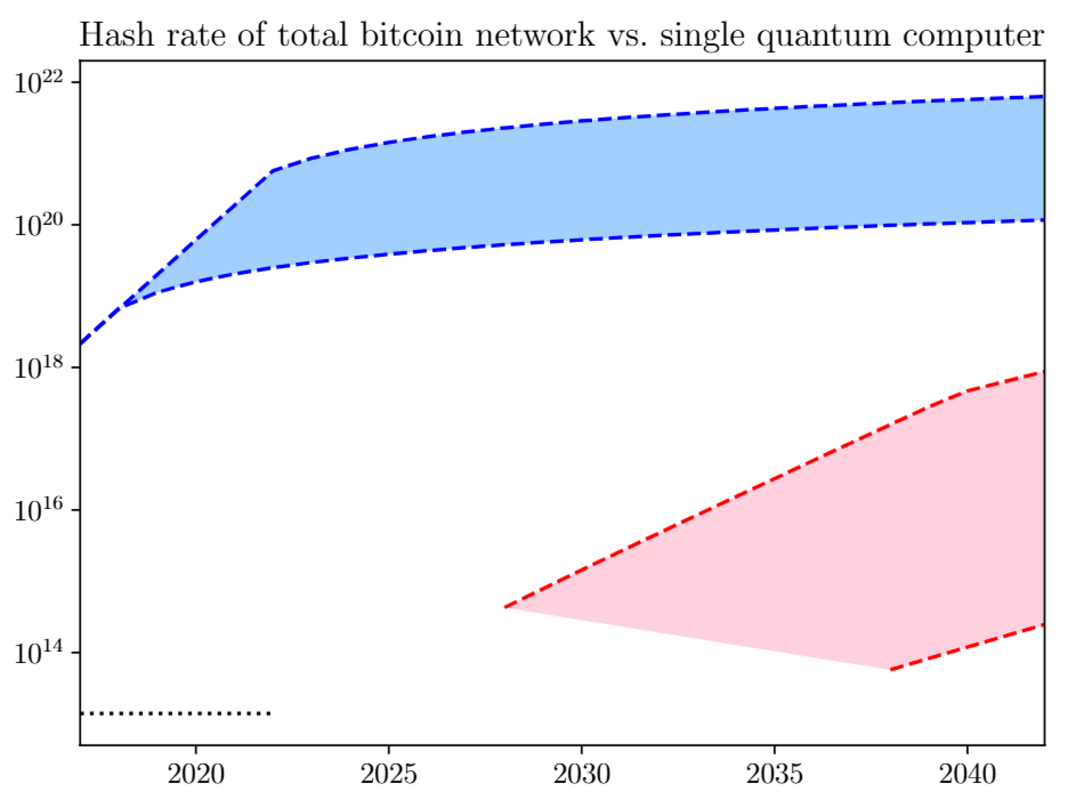
Photo credit: Ledger Journal
Of course, the hashrate of the Bitcoin network has increased tremendously since then, and QC has to deal with decoherence as a major obstacle. But if QEC roadmaps eventually become reliable quantum systems, what can be done to counter the QC threat for Bitcoin?
Quantum Computing Resistance
There are several proposals to protect Bitcoin holders from quantum computers. Since a 51% QC attack is highly improbable, the focus is mainly on hardening wallets. After all, if people can’t trust holding BTC, that’s a reason to run away from Bitcoin.
In turn, the price of BTC drops and the network’s hashrate plummets, making it more vulnerable to QC than previously thought. One such hardening is the implementation of Lamport arms.
with the Lamport signaturesThe private key is generated in pairs, 512-bit strings from the 256-bit output. A public key is generated by a cryptographic function for each of the 512-bit strings. Each BTC transaction requires a one-time Lamport signature.
Because Lamport signatures do not rely on elliptic curves in the finite fields of the Elliptic Curve Digital Signature Algorithm (ECDSA), which is used by Bitcoin and can be used by Ball’s algorithm, but on hash functions, this makes them a viable quantum-resistant alternative.
The downside of Lamport signatures is their large size, above 16KB and single use. Of course, by simply changing addresses and storing BTC in cold storage, avoiding private key exposure also prevents QC efficiency.
Another method of obfuscating potential QC attacks would be to implement network-based cryptography (LBC). Unlike ECDSA, LBC avoids finite models by relying on discrete points in an n-dimensional grid (mesh) space that extends infinitely in all directions. Because of this feature, no quantum algorithm has been developed to break LBC.
However, Bitcoin had to go through a hard fork to implement this new type of cryptography. In this scenario, there should be many signs that quantum computing, especially qubit computing and fault tolerance, will make major breakthroughs.
The bottom line
It can be said that the Bitcoin mainnet itself is not threatened by quantum computing, either in the near or distant future. Still, if QC breaks Bitcoin’s encryption and makes SHA-256 and ECDSA obsolete, it will have a profound impact on trust in the cryptocurrency.
This trust is essential, as demonstrated by major companies such as Microsoft and PayPal, which accept Bitcoin payments. 80% savings compared to card transactionsZero returns, and full control of funds. With more than 300 million holders worldwide, bitcoin’s appeal as a safe asset and cost-effective payment option remains strong.
Ultimately, Bitcoin’s value is supported by the capital and trust behind it. His historical instability shows how things are happening Tweets from Elon Musk and the launch of PayPal’s ETF and the fall of FTX – weighed on market sentiment. A major threat to Bitcoin encryption could be panic selling, withdrawals of miners, and a drop in mining difficulty, which could lead to a 51% QC attack with fewer qubits.
To avoid such a scenario, Bitcoin owners and developers would do well to stay abreast of QC developments.
This is a guest post by Shane Neagle. Opinions expressed are entirely his own and do not necessarily reflect those of BTC Inc or Bitcoin Magazine.
Source link
[og_img]




