How to claim the killing code of millions of people and hundreds of popular apps

It started when I was watching convergean editor of text ai. Also, I use Lulu by purpose-see On my laptop, so when I downloaded the cursor installer, I got this pop-up:
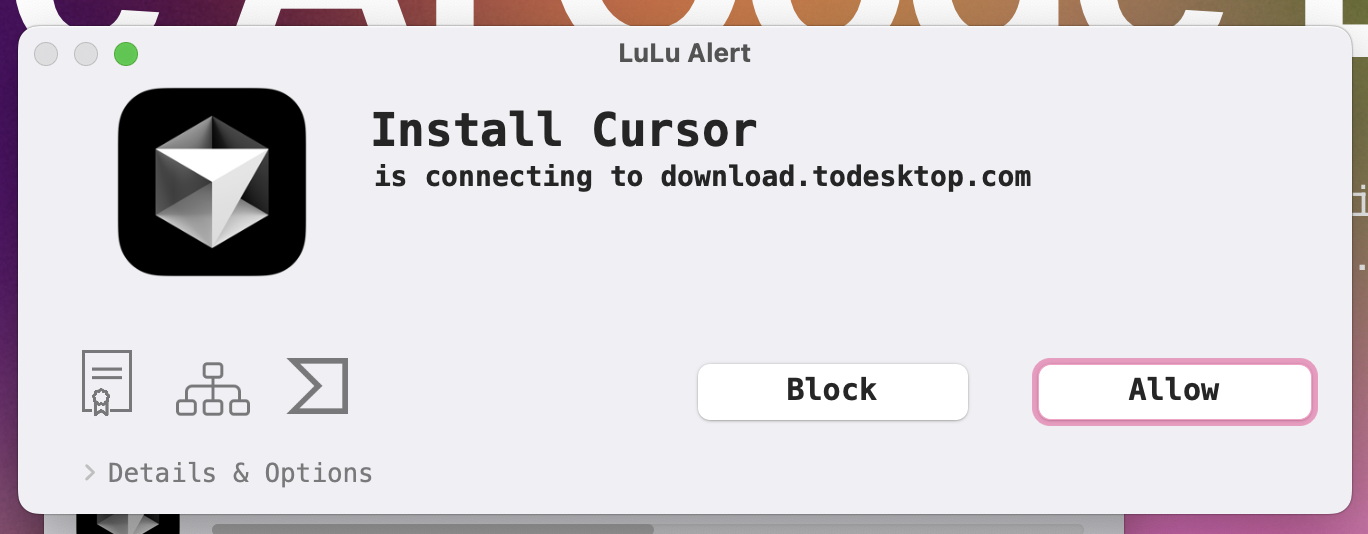
Now, what is hell? I thought I downloaded cursor? Well, looking at their website, as they are a service electron app in the room that provides an SDK for electron apps. So see the installer I downloaded the real todesktop, non cursor.
It makes me surprised and I made a todesktop account to look at it, and if I clicked the Github Login button, I saw my calling: fireworks
Basic Firebase Reconce
The Firebase used app is known (No-SQL Database of Firebase frequently used in PrentTend), I immediately opened my Devtools and started doing the Devtools on Firebase.
I know that site has site source, which makes finding all firststore trails using the app easier (it’s easy to be out of souremaps, usually)
Then I found an insecure collection, temporaryApplicationsWhich seemed to give me an name list of some applications (edit: todesktop has clarified this collection has no sensitive data and hasnt been updated since 2022), but not much other than that, everything seemed secure on the firebase other that.
I noticed that most of deployment and general logic occurred in the terminal, with NPM package @todesktop/cliSo I installed it and started looking at it
View at todesktop cli
The CLI is in charge of deployments, upload source codes, and more. The website as a shell to make applications, see deployment, etc.
I’m sure the CLI also has a source of sources, so I use Sourc folders to get it on a tree.
Looking there, I found an arbitrary upload of S3 Uploaded vulnerability through a firebase Cloud function called getSignedURLBut I never had a S3 key (file file) to upload that to make something interesting, so I keep looking.
Hijacking pipeline pipeline by a postinstall script
I’d like to go to the machine where the application gets built and the easiest way to make it a postinstall script to package.jsonSo I did that in a simple reverse swarming shell payload
It works. Navigation around the room, I think of which actual application to build life code, and finds it:
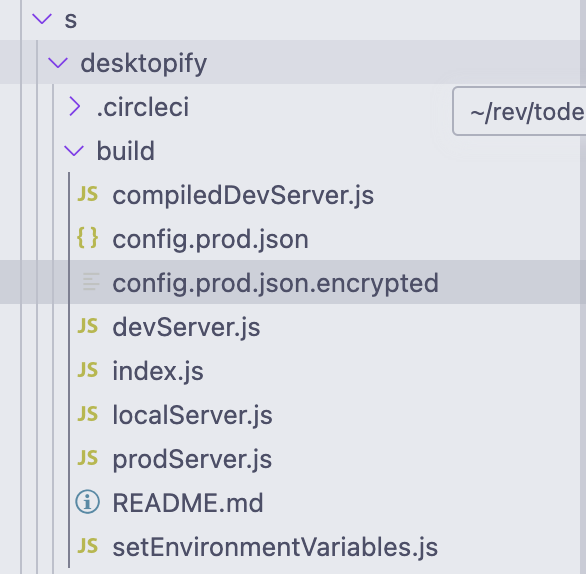
Oh fuck, it usually means something bad. I found the code for decrypting this file, and this is what I got after decrypting it myself:
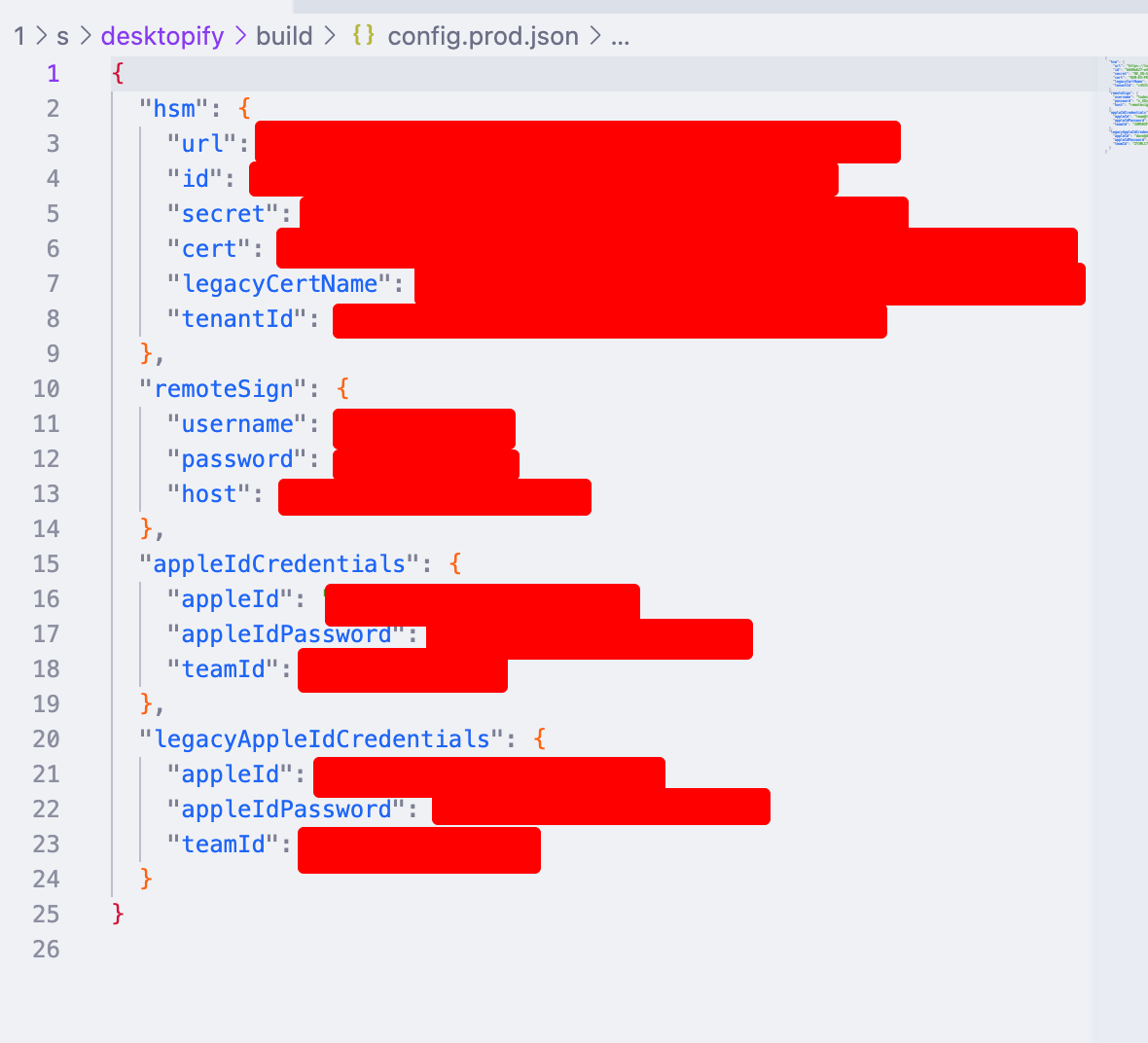
Fuck. These contents of the internal
Looking around the container, I found a hardcoded firebase admin key (full of thickness).
Take advantage of the post
I quickly know that with my credentials, I can update an auto update with any app on my liking, there are clients to receive the app restart immediately.
I made a quick code to use my credentials to update my app, and it worked. I immediately got an update to my client and got RCE.
Allow to talk about impact
With this, I can push the car updates all applications using todesktop, such as:
- Clickup (https://clickup.com)
- Cursor (https://corsor.com)
- linear (https://linear.app)
- Calendar’s mind (https://calendar.notion.so)
(Please do not find these companies or as it seems like it is their mistake, it’s not. This is the Todesktop error if anything)
that, if I estimate, perhaps in many hundreds of millions of people in Tech environmentsother hackers, programmers, executives, and others who make this exploit Deadly when used.
the repair
I immediately used my contacts to reach the TODESKTOP owner, we chatted by signal and healing almost immediately. They are so cute to pay me for my efforts and is very good in general.
Building currently has a privileged sidecar doing all signing, upload and everything instead of the main container with the user code with logic.
Security incidents occurred all the time, natural. The reason is the company’s response, and Todesktop’s response is awesome, they are very good to work.
Check Todesktop event report HERE
2025-03-01 00:05:00